Anthony Timbers: Blog
The Importance of Cybersecurity Awareness Training for Your Employees
As the frequency and severity of cyber attacks continue to rise, it’s more important than ever for businesses to prioritize their cybersecurity. One of the most effective ways to ensure your business is protected is by providing cybersecurity awareness training to your employees.
Read MoreWhy Network Segmentation is Critical for Enterprise Cybersecurity: An In-Depth Guide
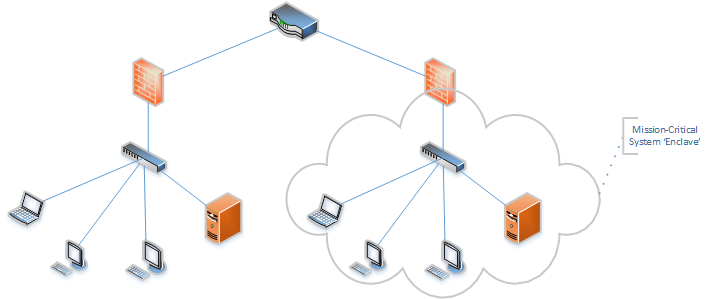
As cyber threats continue to evolve, enterprise cybersecurity is becoming increasingly complex. One of the most effective ways to improve the security of your network is through network segmentation. Network segmentation is the process of dividing a network into smaller, isolated parts to reduce the risk of a security breach.
Read MoreThe Dangers of Cyber Attacks: Why Your Business Needs Managed Cybersecurity Services
In today’s digital age, cyber attacks are becoming increasingly common and sophisticated. From small businesses to large corporations, no company is immune to the dangers of cyber threats. In fact, the frequency and severity of cyber attacks are only increasing, making it more important than ever for businesses to take their cybersecurity seriously.
Read MoreThe Importance of Keeping Software Up-to-Date and How to Stay on Top of Updates: A Comprehensive Guide
Cybersecurity is a critical issue in today’s digital world, and keeping software up-to-date is one of the most important steps you can take to protect your devices and networks. Software updates often contain security patches that address vulnerabilities and fix bugs that could be exploited by cyber criminals. By failing to keep software up-to-date, you run the risk of exposing your devices and networks to potential cyber attacks.
Read MoreWhy Cybersecurity is Critical for Managed IT Services
In today’s digital age, cybersecurity is a critical concern for businesses of all sizes. With the increasing reliance on technology in all aspects of business operations, the threat of cyber attacks and data breaches has never been higher. As technology continues to advance, so do the methods and tactics of cybercriminals, making it essential for businesses to stay ahead of the curve when it comes to protecting their sensitive information. In this blog, we will explore why cybersecurity is critical for managed IT services and why every business should consider it a top priority.
Read MoreThe Importance of Managed Cybersecurity Services for Businesses
As technology continues to evolve and cyber threats become increasingly sophisticated, it’s more important than ever for businesses to take their cybersecurity seriously. With so much sensitive information being stored and transmitted online, it’s essential to have a strong defense against potential cyber attacks.
Read MoreUnderstanding Phishing Scams and How to Avoid Them
Phishing scams are a common tactic used by cyber criminals to gain access to sensitive information, such as login credentials, personal information, and financial data. These scams often come in the form of emails, text messages, or phone calls, and appear to be from a reputable source, such as a bank, online retailer, or government agency.
Read More5 Key Benefits of Managed IT Services for Small Businesses
Small businesses often face a unique set of challenges when it comes to managing their technology and ensuring their systems are secure, efficient, and reliable. This is where managed IT services come in. In this blog, we will explore the five key benefits of managed IT services for small businesses.
Read MoreThe Risks of Public Wi-Fi and How to Stay Safe
Public Wi-Fi networks, such as those found in coffee shops, airports, and hotels, can be convenient, but they also pose a significant security risk. Public Wi-Fi networks are often unsecured, meaning that anyone on the network can potentially intercept data transmitted over the network, including login credentials, personal information, and financial data.
Read MoreCybersecurity Threats: A Guide for Businesses
In today’s digital age, businesses of all sizes are at risk of cyber threats. From data breaches to ransomware attacks, it’s important for companies to be proactive in protecting themselves from the potential dangers that exist online. One of the…
Read More- « Previous
- 1
- 2
- 3
- Next »